Yes, We Speak Tech, Too!
At Timeless Medical Systems®, we understand the importance of seamless integration and rock-solid security when it comes to software solutions. That’s why our software is built to integrate with many external systems, including LDAP(S), SSO solutions and all major EHR systems using HL7. Our software is designed to work with your existing infrastructure, making it easy to get up and running quickly. And with security and trust built in from the ground up, you can rest assured that your data is safe and secure.

Timeless Medical Software Solutions Fully Supports






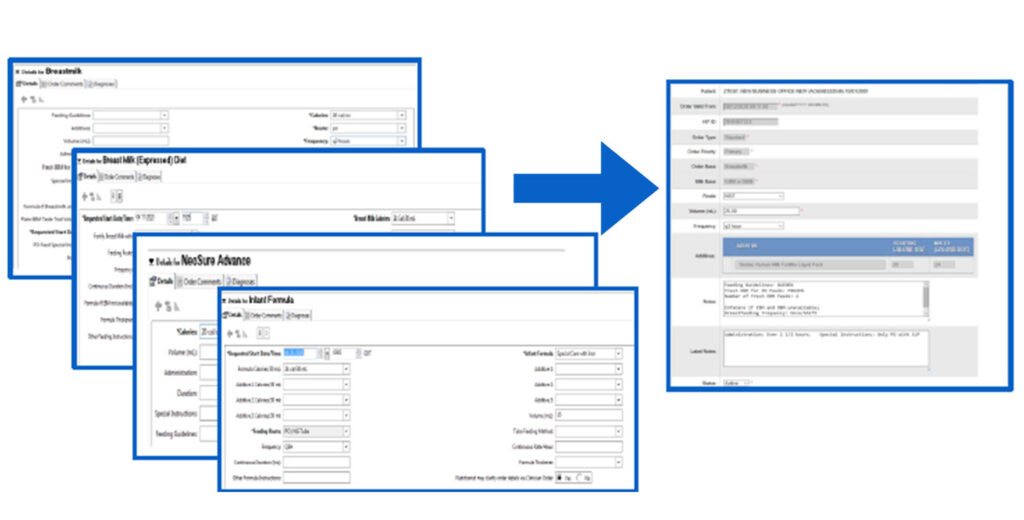
All Cerner Order Types Interface & Translate into Timeless


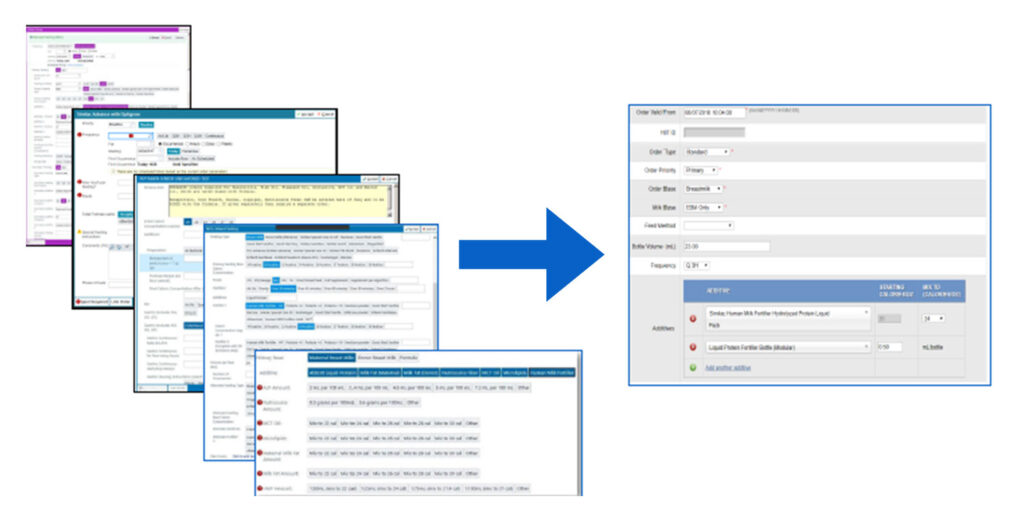
All EPIC Order Types Interface and Translate into Timeless
BUILT WITH SECURITY & TRUST
At Top Of Mind
It isn’t just HIPAA we understand, but risks of patient data as we continuously evaluate and strengthen our security.
BUSINESS ASSOCIATE AGREEMENTS
Timeless Medical Systems® signs business associate agreements (BAAs) with our third-party vendors to ensure security obligations and data protection.
ePHI RESTRICTED
Access to information systems that house ePHI is based strictly on business needs only. Accounts are set up based on least-privilege access for their job function. All accounts are individual and associated to a person.
CULTURE OF SECURITY
All employees complete mandatory HIPAA and security training upon hire and annually thereafter.
BUILT WITH SECURITY & TRUST
At Top Of Mind
In today’s digital landscape, where data breaches pose significant threats, here at Timeless Medical Systems® our commitment to security is resolute. Utilization of enterprise-grade best practices, working with independent experts to verify our security, privacy, and compliance controls to achieve SOC 2 Type 2 and HIPAA compliance of stringent standards ensures that our organization maintains the highest standards in safeguarding sensitive data and upholds the trust of our clients and stakeholders.
This proactive approach not only demonstrates our commitment to maintaining a robust cybersecurity posture but also underscores our accountability in handling confidential information within the healthcare sector. SOC 2 Type 2 and HIPAA compliance are not just benchmarks; they signify our continual efforts to evolve and adapt to the dynamic landscape of information security, ensuring that our systems and processes consistently meet or exceed industry standards.
As we navigate the complex terrain of data protection, we remain vigilant in addressing emerging threats and evolving regulatory requirements. Our investment in these compliances reflects our organizational ethos of prioritizing the security and privacy of the data entrusted to us. Clients and partners can rest assured that our commitment to excellence extends beyond providing exceptional products and services; it encompasses the establishment and maintenance of a secure and compliant environment that aligns with the highest industry standards.
With Drata, Timeless Medical Systems® has real-time visibility across the organization to ensure the end-to-end security and compliance posture of our systems. Automated alerts and evidence collection allows Timeless Medical Systems® to confidently prove its commitment to protecting your sensitive health information any day of the year, while fostering a security-first mindset and culture of compliance across the organization.
In the spirit of openness, transparency and partnerships with our customers in data privacy and security, here are some of the security measures we take to protect our customers’ sensitive information.
BUSINESS ASSOCIATE AGREEMENTS
Timeless Medical Systems® signs business associate agreements (BAAs) with our third-party vendors to ensure security obligations and data protection.
ePHI RESTRICTED
Access to information systems that house ePHI is based strictly on business needs only. Accounts are set up based on least-privilege access for their job function. All accounts are individual and associated to a person.
CULTURE OF SECURITY
All employees complete mandatory HIPAA and security training upon hire and annually thereafter.
Where applicable by law, Timeless Medical Systems® performs background screenings on personnel prior hiring. Two-factor authentication is enforced for sensitive data systems. Approved password managers to generate and store single use passwords are required. Company owned devices are encrypted, screen locked enabled, receive auto-updates, and anti-virus scanning.
PRODUCT SECURITY
Security is incorporated into the design of our products during the software development life cycle along with vulnerability scanning. We have an established Change Management Process that is followed.
DATA PROTECTION
With Strict Transport Security Header (HSTS), we prioritize the protection of your information, keeping data safer and more secure while in transit. At rest data is also protected with industry standard encryption.
PENETRATION TESTING
In addition to development-related testing, we conduct third party manual penetration testing of our applications and infrastructure at least annually.
It is common for our team to fill out IT security and technical review documents provided to us by our prospective customers to make it easy for them to evaluate our software. Please feel free to fill out the form below to initiate this review process or to ask any additional questions. Reports available with signed NDA.
Speak with an IT expert
Our technology team is ready to answer any questions
you might have regarding our software, integrations, implementation or security.



